Supplier Risk & Performance Real-time, AI-driven monitoring of your entire supplier base
Explore Supplier Risk & Performance features
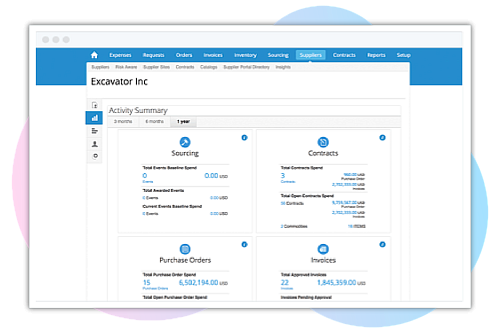
Drive supplier adoption with self-service
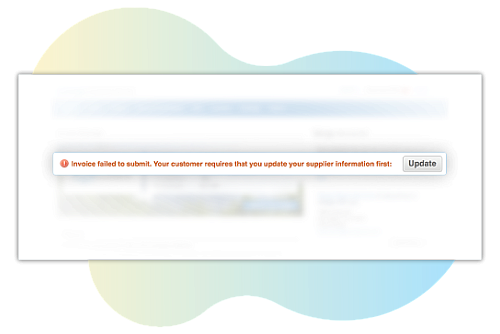
An intuitive portal makes it easy for suppliers to send updates when receiving a PO or sending an invoice. Any invoice submissions with missing information come with an automatic warning or are blocked, followed by an alert to the supplier to complete the missing areas – no action required on your end.
Learn more about Supplier Information Management
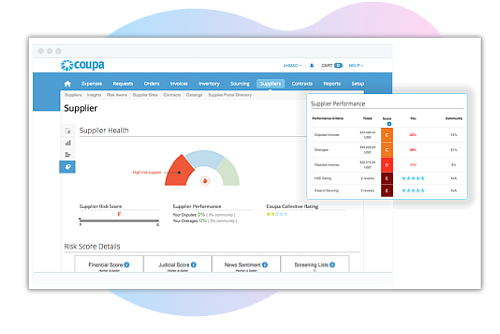
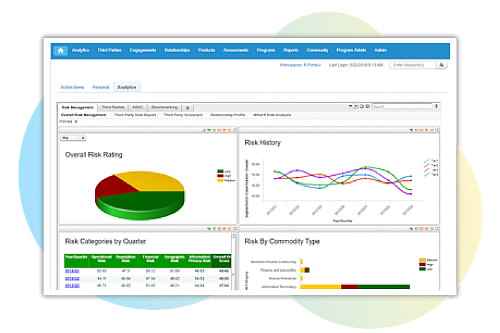
View risk comprehensively from one place
Use AI to flag issues by continuously monitoring outside data sources, cross-community, and user-submitted performance feedback. When ratings change, take action with prescriptive recommendations, such as putting high-risk suppliers on hold or reviewing alternative suppliers.
Put risk detection on auto-pilot
Digitize and automate your suppliers’ third-party risk across InfoSec, Anti-Bribery Anti-Corruption (ABAC), GDPR, and many other domains — even as new risks emerge. If a supplier's risk increases, get real-time alerts and intelligent recommendations on the next best steps.
Make DEI a priority
Maximize your diversity, equity, and inclusion (DEI) impact while minimizing costs. Embed diversity in sourcing criteria, access a database of over 2 million certified minority-, women-, veteran- and LGBT-owned vendors, and track your company’s spending with diverse suppliers all from one place.
Learn more about Supply Chain Diversity